Lab 3-2 | Practical Malware Analysis
For this one lab I chose to first follow the book’s guide on the first dynamic analysis, since the mix of all the programs and parameters you have to look after can become a bit too overwhelming if you’re a n00b like me :)
I want to make clear too that I do my static analysis, but I usually prefer to just answer the questions and bring up what I found during SA only when it’s necessary.
Anyways, I also won’t be going into much detail like I did in the static analysis labs’ section just because it’s DA practice time, but I’ll still include definitions which I consider revealing or important. I will, however, attach links to definitions.
***Before starting***: take a snapshot of the VM with all the software installed, the inner network configured and without having run any malware sample yet, you’ll need it to revert back after you’re done with this sample.
1. How can you get this malware to install itself?
From the export functions table, we can see a few functions that will be exported by this malware.
Anyways, we also discovered that it was running as a service.
At this point, another question popped: what would be the difference between a service and a process in the Windows world?
From this page here, a process is just an instance of an executable running, while a service will be started by the OS and will be running in the bakground, which is what we traditionally call a daemon.
After that keys added, we get into the section of added values. Here, we can see that this piece of malware added a path to svchost.exe to launch itself, since it is a DLL and will need an executable to launch itself.
According to Microsoft:
Svchost.exe is a generic host process name for services that run from dynamic-link libraries.
That is helpful!
Now we know this malware will make use of this generic executable to launch itself.
2. How would you get this malware to run after installation?
So we know already that it will make use of a service, the IPRIP service, and therefore we will need to run it as a service. However, when we examine the strings we find another problem.
Hm, it can’t find its service name? Too bad :(
We’ll have to find a way to get around this, so what about looking up what’s in that registry key? Maybe we can find useful services.
6to4 will do! It’s a network service we can use to run our malware instead of using the IPRIP service.
rundll32.exe Lab03-02.dll,installA 6to4
And then our malware will be installed as a service :)
Now that it’s installed, we should run it, shouldn’t we?
So, to view the network connections for further network-based indicators, we will set up apacheDNS to listen to the Linux VM, which we in turn configured with netcat, wireshark and inetservice ( I later discovered I didn’t need it, but it’s okay as it doesn’t interfere ).
Okay, the last step is to start the IPRIP service with ‘net start IPRIP’ and hope for the best.
Success!! :D
3. How can you find the process under which this malware is running?
Here I used the Find > Find DLL feature of process explorer to find the DLL, and then looked for the PID number I saw in question #3.
4. Which filters could you set in order to use procmon to glean information?
As we can see, the PID is 2648.
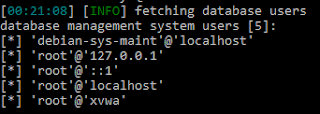
5. What are the malware’s host-based indicators?
In the strings section we can find the first line to be very adequate to use as a host-based indicator:
6. Are there any useful network-based signatures for this malware?
Netcat received the DNS request from the Windows VM, and Wireshark could capture the HTTP request, so there we have it.
www.practicalmalwareanalysis.com is a perfect network based indicator :)
Finally, do not forget to revert to the snapshot you had right before you ran the malware.










Lab 3-2 offers a hands-on approach to dynamic malware analysis, highlighting how services like IPRIP can be exploited to run malicious DLLs. Tools like NAPS2 malware analysis, though not designed for this, remind us why understanding legitimate vs. suspicious software is crucial.
ReplyDelete