Lab 1-4 | Practical Malware Analysis
1. Upload the Lab01-04.exe file to http://www.VirusTotal.com/. Does it match any existing antivirus definitions?
2. Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
After observing the files just like the other labs, I concluded that, due to the number of functions imported and the Virtual Size and the Raw Data size not being so different, this one executable is not packed.
3. When was this program compiled?
So… I looked at the compilation time and…
4. Do any imports hint at this program’s functionality? If so, which imports are they and what do they tell you?
In this executable we can find ADVAPI32.dll, KERNEL32.dll and MSVCRT.dll.
In ADVAPI32.dll we start by seeing the function OpenProcessToken, LookUpPrivilegeValueA and AdjustTokenPrivileges.
The OpenProcessToken, from MSDN:
What do they mean by access token? Well, MSDN also helps us with that.
Oh? So it’s looking for our access token for a certain process? I already dislike this.
Now for the LookUpPrivilegeValue:
And the LUID?
Finally, AdjustTokenPrivileges:
So ADVAPI32.dll is all about the privileges on the system, as we can see from here. And this sample is trying to perform activities just as it it was the user.
Let’s find out which actions is it trying to perform.
In KERNEL32.dll we could find a thousand and one functions, so I’ll try to be concise about it.
The GetProcAddress will get the address of an exported function and LoadLibraryA will just do what it says. WinExec will execute an application.
After reading from MSDN that WinExec would execute an application, I wondered if there could be a GUI. Maybe it doesn’t have anything to do with it, but what if…
5. What host- or network-based indicators could be used to identify this malware on infected machines?
6. This file has one resource in the resource section. Use Resource Hacker to examine that resource, and then use it to extract the resource. What can you learn from the resource?
2. Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
After observing the files just like the other labs, I concluded that, due to the number of functions imported and the Virtual Size and the Raw Data size not being so different, this one executable is not packed.
3. When was this program compiled?
So… I looked at the compilation time and…
Surprise! Back to the future!
This compilation time has been clearly modified to make analysis more difficult. I wonder if we can find the real date somewhere in this executable...
4. Do any imports hint at this program’s functionality? If so, which imports are they and what do they tell you?
In this executable we can find ADVAPI32.dll, KERNEL32.dll and MSVCRT.dll.
In ADVAPI32.dll we start by seeing the function OpenProcessToken, LookUpPrivilegeValueA and AdjustTokenPrivileges.
The OpenProcessToken, from MSDN:
The OpenProcessToken function opens the access token associated with a process.
What do they mean by access token? Well, MSDN also helps us with that.
An access token contains the security information for a logon session. The system creates an access token when a user logs on, and every process executed on behalf of the user has a copy of the token.
Oh? So it’s looking for our access token for a certain process? I already dislike this.
Now for the LookUpPrivilegeValue:
The LookupPrivilegeValue function retrieves the locally unique identifier (LUID) used on a specified system to locally represent the specified privilege name.
And the LUID?
(LUID) A 64-bit value that is guaranteed to be unique on the operating system that generated it until the system is restarted.
The AdjustTokenPrivileges function enables or disables privileges in the specified access token.
So ADVAPI32.dll is all about the privileges on the system, as we can see from here. And this sample is trying to perform activities just as it it was the user.
Let’s find out which actions is it trying to perform.
In KERNEL32.dll we could find a thousand and one functions, so I’ll try to be concise about it.
The GetProcAddress will get the address of an exported function and LoadLibraryA will just do what it says. WinExec will execute an application.
After reading from MSDN that WinExec would execute an application, I wondered if there could be a GUI. Maybe it doesn’t have anything to do with it, but what if…
Oh hey! Look, there’s a GUI right there!
So with the CreateFileA we could assume it only creates a file, but we should be careful, because it can also create I/O streams, physical disks, communications resources, mailslots…
SizeOfResource will retrieve the size of the resource we tell it in bytes.
About CreateRemoteThread:
Creates a thread that runs in the virtual address space of another process.
Suspicious, right? Let’s keep digging.
With GetModuleHandle we’ll get a handle of the specified module, GetWindowsDirectory will get the path of the Windows directory, MoveFileA will get a file or directory and its children and move it, GetTempPath will get the path where the temporary files are stored, GetCurrentProcess retrieves a “pseudo” handle of the current running process.
Note: a pseudo handle is a handle that can only be valid for the current process, and it can’t be inherited or duplicated by other processes.
OpenProcess will open an existing running process and CloseHandle will close an open handle.
LoadResource does this:
Retrieves a handle that can be used to obtain a pointer to the first byte of the specified resource in memory.
Shady.
So this program will do something like opening files and reading files, just like it executes them with the proper permissions. It also moves files from the Windows directory and gets information from the temporary files.
Both host based and network based indicators can be found in this executable.
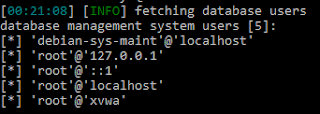
For host based, I found an executable which we could use to detect this sample in the wild.
Wupdmgr.exe would be a perfectly valid way to identify the malware.
And from here, we can see that it also communicates with some server in hxxp://www.practicalmalwareanalysis.com/updater.exe. That’s our network based identifier.
But wait a second, how come there are network identifiers in here… and we haven’t seen any network function? That’s very weird.
6. This file has one resource in the resource section. Use Resource Hacker to examine that resource, and then use it to extract the resource. What can you learn from the resource?
Okay so, what if our sample got hidden resources inside it which we couldn’t see at first
sight? I would like to know if there’s something hidden in my files!
Well, Resource Hacker does just that. We will dissect our sample and look inside.
So we open our executable in RH, right click and save as resource when we see the resource that we’ll most def see.
And if we wanted a network related function, here it comes to the rescue so you don’t go to sleep unfullfilled.
Check the bottom part URLDownloadToFileA, which downloads the bits from the internet and saves them into the file of choice, and then with the help of WinExec, it will execute the file.
By the way, one last thing, what the heck is this ‘This program can’t run in DOS mode’ we’re getting everywhere? It was driving me insane.
So apparently it’s a message that it’s displayed in every Windows PE header, intended to be shown when you try to run the program on something like MS-DOS.
It can also be shown if you try to run the program in a version of Windows which is more advanced than the one for which it was built, but that’s not our case.










Comments
Post a Comment