OverTheWire Natas 11 to 12 || Remote File Inclusion
I am probably starting way too far in the list of challenges. People nowadays have this tendency to start at 'one' or 'zero' when they have a long list of infinite numbers to choose from. Crazy, right?
Well, actually, I am starting from this point mostly because I started doing those way before I made this blog. So now that I'm excused, I'll start.
Interpreting a bit
Right after we enter the creds for this natas level, we're welcomed with an image uploader.
At this point, me and quite a few people, already know what this is about. This challenge will be about RFI or Remote File Inclusion.
~~~ Explanation alert ~~~
Remote File Inclusion (RFI) is an attack that starts from a poorly protected file uploader.
What a black hat hacker intends with this attack is to upload a script that will give her unauthorized information and/or the ability to modify information.
Normally the way to go is, the attacker encounters a file uploader (generally for images, but also text files of various kinds) and uploads a file, let's say, for the sake of this challenge, that it is a PHP backdoor. When the file is uploaded, the web server will think it's hosting an image, but it's actually hosting a PHP script that is listening for outside orders, commands or connections.
How does the web server even possibly think this document is an image? - you ask.
Well, first of all, web servers don't think. So mind you.
Secondly, it does so after the attacker has specified this document will be an image, but at the last moment, it modifies the HTTP request and substitutes the (for example) .jpg extension for .php. You'll understand easily, I took screenshots *wink*.
So let's end this confusing explanation and add a lot of images to this buzzy word-tangle.
~~~~~~~~~~~~~~~~~~~~
This is how I found the website:
It made very clear what it wanted. So now let's view the sourcecode.
That's a lot of code, but worry not, I'll try to be as light as possible.
In the first image there are two hidden inputs, the first one is to specify the file size. The second one is to create a new random string for the filename.
getRandomString() will create this random file name, makeRandomPathFromFilename() creates a random file path using the filename and extension.
Nothing is checked here, they just modify whatever extension you give them (if you upload a .php file) and change it to .jpg instead. So if we uploaded shell.php, the result would be something like ffj49r490.jpg.
I'm not really going to dig deeper into the script, there's not much else really. But if someone wants to look further into it and understand everything that is going on there, I strongly encourage it.
Into action
I downloaded a simple PHP backdoor from Github and uploaded it, then, right before I clicked the Upload button, I popped open Burp Proxy. I set the intercept to 'ON' and the clicked the Upload button.
Here we can see all the data that was being sent to be uploaded as an image. In line 33 you can see it is being uploaded as a random alphanumeric string with the .jpg extension, just as stated and like we read in the source code.
Now this is important: I started to modify the hex code in order to change the .jpg extension. The goal here is to make it a .php extension so we can execute it. Burp Proxy comes handy because it makes the process easier and smoother, so we can tamper with the data being sent and received to and from the server.
There, changed it with the help of a table Char to Hex brought to us by Google Images.
Okay, now that we changed those three extension characters, it's time to forward the request and see if it worked.
:D
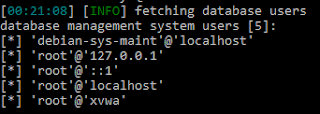
Let's click on that link and open our present.
The script author was even so kind as to add comments for smoother usage.
And basically that's it.
I did a bit of reading for this challenge in http://resources.infosecinstitute.com , so if someone wants to check it out, do it. No time wasted.
Well, actually, I am starting from this point mostly because I started doing those way before I made this blog. So now that I'm excused, I'll start.
Interpreting a bit
Right after we enter the creds for this natas level, we're welcomed with an image uploader.
At this point, me and quite a few people, already know what this is about. This challenge will be about RFI or Remote File Inclusion.
~~~ Explanation alert ~~~
Remote File Inclusion (RFI) is an attack that starts from a poorly protected file uploader.
What a black hat hacker intends with this attack is to upload a script that will give her unauthorized information and/or the ability to modify information.
Normally the way to go is, the attacker encounters a file uploader (generally for images, but also text files of various kinds) and uploads a file, let's say, for the sake of this challenge, that it is a PHP backdoor. When the file is uploaded, the web server will think it's hosting an image, but it's actually hosting a PHP script that is listening for outside orders, commands or connections.
How does the web server even possibly think this document is an image? - you ask.
Well, first of all, web servers don't think. So mind you.
Secondly, it does so after the attacker has specified this document will be an image, but at the last moment, it modifies the HTTP request and substitutes the (for example) .jpg extension for .php. You'll understand easily, I took screenshots *wink*.
So let's end this confusing explanation and add a lot of images to this buzzy word-tangle.
~~~~~~~~~~~~~~~~~~~~
This is how I found the website:
It made very clear what it wanted. So now let's view the sourcecode.
That's a lot of code, but worry not, I'll try to be as light as possible.
In the first image there are two hidden inputs, the first one is to specify the file size. The second one is to create a new random string for the filename.
getRandomString() will create this random file name, makeRandomPathFromFilename() creates a random file path using the filename and extension.
Nothing is checked here, they just modify whatever extension you give them (if you upload a .php file) and change it to .jpg instead. So if we uploaded shell.php, the result would be something like ffj49r490.jpg.
I'm not really going to dig deeper into the script, there's not much else really. But if someone wants to look further into it and understand everything that is going on there, I strongly encourage it.
Into action
I downloaded a simple PHP backdoor from Github and uploaded it, then, right before I clicked the Upload button, I popped open Burp Proxy. I set the intercept to 'ON' and the clicked the Upload button.
Here we can see all the data that was being sent to be uploaded as an image. In line 33 you can see it is being uploaded as a random alphanumeric string with the .jpg extension, just as stated and like we read in the source code.
Now this is important: I started to modify the hex code in order to change the .jpg extension. The goal here is to make it a .php extension so we can execute it. Burp Proxy comes handy because it makes the process easier and smoother, so we can tamper with the data being sent and received to and from the server.
There, changed it with the help of a table Char to Hex brought to us by Google Images.
Okay, now that we changed those three extension characters, it's time to forward the request and see if it worked.
:D
Let's click on that link and open our present.
The script author was even so kind as to add comments for smoother usage.
And basically that's it.
I did a bit of reading for this challenge in http://resources.infosecinstitute.com , so if someone wants to check it out, do it. No time wasted.







Comments
Post a Comment